Beware Window 10 Upgrade Phishing Scam
A campaign is in progress as of this writing targeting Windows 8 users who have yet to receive the “Get Windows 10” app icon. Users that open the email, unzip, and run the attached executable are soon greeted by a ransomware variant called CTB-Locker.
A campaign is in progress as of this writing targeting Windows 8 users who have yet to receive the “Get Windows 10” app icon. Users that open the email, unzip, and run the attached executable are soon greeted by a ransomware variant called CTB-Locker.
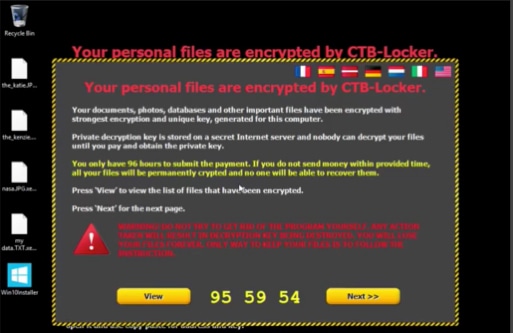
The message reads in part, “Your personal files are encrypted by CTB-Locker…Private decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the private key. You only have 96 hours to submit the payment.”
From grandma to my wife to my nephew, I have to tell you that the Windows 10 upgrade was quite the buzz around our family last weekend. We might be a little atypical in that even grandma was a former techie; regardless the potential for scammers to exploit excited Windows users is evident.
? As a best practice, backup important data now and on a recurring basis to a device that can store it offline. Detachable USB drives are excellent and inexpensive options.
? Paid for cloud-storage services like Dropbox, Google Drive, or OneDrive provide some protection in the form of storing version history and being able to retrieve copies of past versions. However, be careful, last I knew OneDrive only stored past versions of Office documents and not those precious baby pictures! Also, the headache of having to revert hundreds of files does not sound like a fun weekend to me.
? Educate yourself and company employees.
? Implement company-wide email attachment scanning software. Or, be sure to save attachments to a disk before opening them and ensure a reputable antivirus program is kept up-to-date to scan those attachments.
A couple of weeks ago, I completed a consulting assessment for a company that included their use of firewalls, antivirus software and sophisticated intrusion-detection systems. Beyond the expected bad actors seeking financial or personal gain, there are so many other avenues that put companies at risk. End users who violate security policy (you know who you are) and development teams oblivious to common security flaws introduced by their code are but two examples that we’ll have to hold for another time. Until then, please be cognizant of how social engineering attacks can cause incredible mayhem. Hackers are counting on you to be the weakest link in the computer security chain and, if you read this far, you certainly know better!
By Paul Schroeder, Solutions Architect